Mikrotik Sniffer
Mikrotik Sniffer, Packet sniffer is a tool that can capture and analyze packets that are going to, leaving or going through the router.
Note: Unicast traffic between Wireless clients with client-to-client forwarding enabled will not be visible to sniffer tool. Packets that are processed with hardware offloading enabled bridge will also not be visible (unknown unicast, broadcast and some multicast traffic will be visible to sniffer tool).
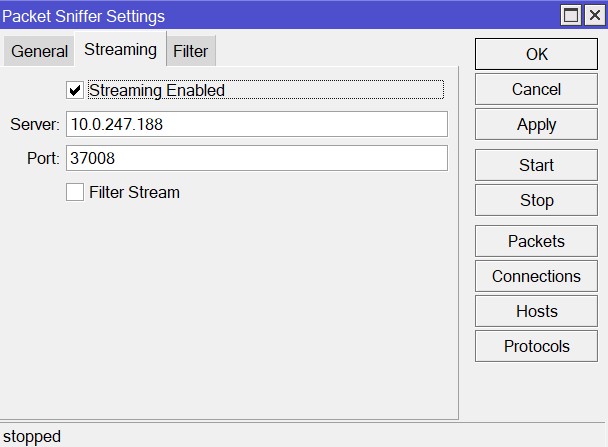
In the following example streaming-server will be added, streaming will be enabled, file-name will be set to F660 and packet sniffer will be started and stopped after some time:
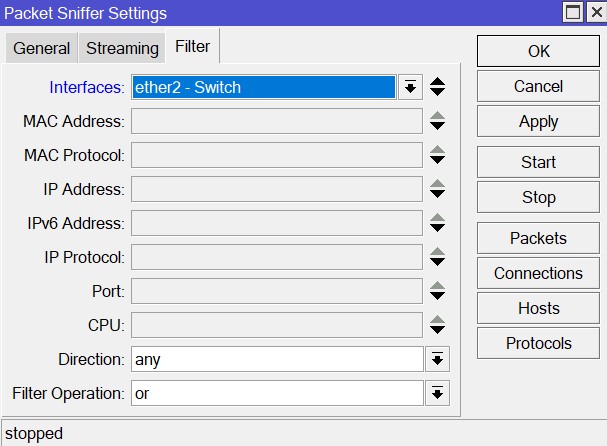
Filter is used to specify the interface or Device (by MAC, IP…), in our case we will scan everything on interface ether2 – Switch:
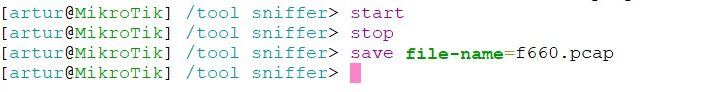
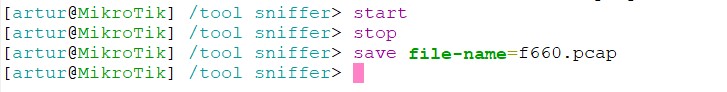
The commands are used to control runtime operation of the packet sniffer. The start command is used to start/reset sniffering, stop – stops sniffering. To save currently sniffed packets in a specific file save command is used.
Below the sniffed packets will be saved in the file named f660.pcap:
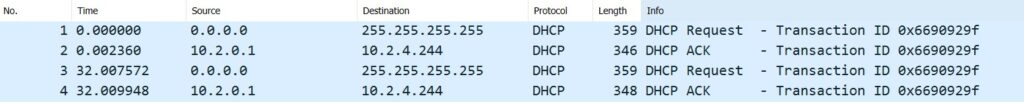
To Open the file that is scanned move it to your desktop and open it with Wireshark.